The 10 Hottest New Cybersecurity Tools And Products Of 2021
The 10 cybersecurity tools and products making an impact deliver everything from ransomware readiness assessments and automated incident investigations to protection for remote workers and small businesses.

Taking On Tomorrow’s Threats
See the latest entry: The 10 Coolest Cybersecurity Tools and Products In 2022 (So Far)
Vendors have spent 2021 advancing security everywhere from endpoint and identity to the cloud and web, debuting tools that respond to threats across the criminal underground, protect remote workers‘ homes and small businesses from malware, ransomware and phishing attacks, and allow for the management of access, governance and privileges from a single, centralized dashboard.
Enhancements to security operations and intelligence have been a major area of focus thus far in 2021, with advancements around everything from and managed account takeover monitoring and automating incident investigations with actionable insight to assessing an organization’s readiness for ransomware and using data to drill into granular details of past and present attacker activity.
Seven of the 10 hottest cybersecurity tools and products of 2021 (so far) came from companies based in California, with the remaining three coming from vendors based in Colorado, Minnesota and England and Israel. Read on to learn how vendors have gone about making their cybersecurity portfolio even more solution- provider-friendly.
For more of the biggest startups, products and news stories of 2021, clickhere.
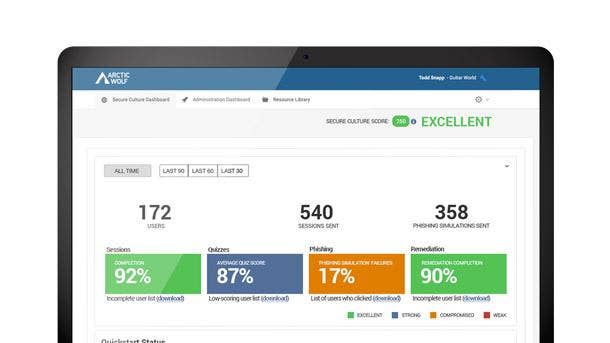
Arctic Wolf Managed Security Awareness
Arctic Wolf Managed Security Awareness debuted in May and brings together fully managed security awareness training, phishing simulation and account takeover monitoring that’s delivered as a concierge service. It’s intended to make it fast and easy for all security teams, including those who don’t have an IT or cybersecurity function, to add a security awareness and training program.
Eden Prairie, Minn.-based Arctic Wolf’s offering includes security awareness microlearning that prepares employees to stop social engineering attacks with continuous training to recognize current threats, avoid scams and understand the importance of reporting mistakes. Account takeover monitoring, meanwhile, reduces risk with immediate notification when employee credentials are found on the dark web.
The phishing simulation capabilities measure and reinforce employee awareness with automated assessments and phishing simulations based on real-life attacks. And turnkey content delivery engages employees by deploying timely content with high production value and a vision of building academic-level programming rigor.
Check Point Harmony
Check Point Software Technologies in February rolled out the Harmony unified offering to secure both internet connections as well as corporate and BYOD devices for remote workers. The platform brings together endpoint, browser, email and remote access security into a single offering that’s managed via a cloud service and is available to customers for $11 per user, per month.
The all-new Harmony Browse tool provides secure, fast and private web browsing by inspecting all SSL traffic directly on the endpoint without adding latency or re-routing traffic through a secure web service, according to San Carlos, Calif.-based Check Point. It blocks zero-day malware downloads and access to phishing websites as well as preventing the reuse of corporate passwords, according to the company.
Other elements of the Harmony bundle include Connect, which Check Point said securely connects any user or branch to any resource, supporting clientless zero trust network access from any browser. All Harmony products—including the rebranded Harmony Email and Office and Harmony Endpoint—can be managed from a single portal, simplifying the day-to-day experience for users and administrators alike.
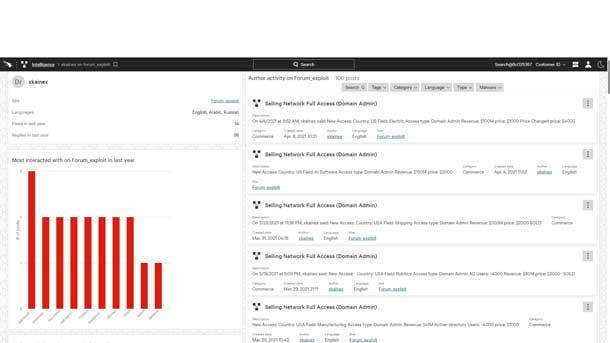
CrowdStrike Falcon X Recon+
CrowdStrike Falcon X Recon+ debuted in July to simplify the process of hunting and mitigating external threats against brands, employees and sensitive data. Falcon X Recon+ threat experts manage digital risk protection efforts by monitoring, triaging and assessing the response to threats across the criminal underground, enabling customers to focus on their business, the Sunnyvale, Calif.-based company said.
Falcon X Recon+ experts monitor data from thousands of restricted forums, marketplaces, messaging platforms, social media posts and data leak sites to provide relevant real-time warnings, identifying data exposure and threats to the enterprise. The offering delivers visibility into cybercriminal activity that goes beyond the internet to include botnet, DDoS configurations and messaging applications.
Falcon X Recon+ experts work on the customer’s behalf to identity and facilitate the takedown of fraudulent accounts, phishing websites, domains and malicious posts that potentially harm a business’ reputation. Customers are also invited to the CrowdStrike Quarterly Threat Brief, where the company’s experts provide insight into current and trending activity across the threat landscape, the company said.

Fortinet FortiTrust
Fortinet’s FortiTrust security services debuted in July and offer user-based licensing across all networks, endpoints and cloud, with a focus on zero trust network access and identity verification. FortiTrust’s user-based licensing eliminates the need to track device counts or bandwidth consumption and makes it easy to calculate total cost with built-in volume discounts, the Sunnyvale, Calif.-based company said.
FortiTrust’s initial services portfolio includes FortiTrust Access and FortiTrust Identity with additional service options for SASE, CASB and endpoint protection platforms expected to be released. FortiTrust Access enables organizations to deploy zero trust network access with user-based pricing, which is crucial to maintaining consistent protection, visibility and control across highly distributed networks.
FortiTrust Identity, meanwhile, offers cloud-based multifactor authentication for identity verification while also providing the multifactor authentication needed to control application access. All told, Fortinet said FortiTrust provides organizations with a unified services offering to protect any network, endpoint or cloud with a simplified consumption and single licensing model for all form factors.
Mandiant Ransomware Defense Validation
Mandiant Ransomware Defense Validation debuted in October and allows ransomware types to be tested in customer environments in safe ways to determine whether the customer’s existing controls can stop an attack. It’s an entry-level offering derived from the broader Mandiant Security Validation module focused specifically on understanding an organization’s readiness for ransomware.
Mandiant traditionally required a virtualized environment to run ransomware, but with Ransomware Defense Validation is able for the first time able to test ransomware in a production environment by using malware reversers. The module offers not only the same level of technology and reporting as Security Validation, but also includes Mandiant experts to run the test and decide what’s a priority.
With Ransomware Defense Validation, Milpitas, Calif.-based Mandiant experts run the test and explain the results to the customers rather than directing the customer to conduct the exercise themselves. The tool provides more narrow content, reporting and views than Mandiant Security Validation, which should make it more affordable and digestible for smaller organizations.
Okta Privileged Access and Identity Governance
Okta customers early next year will be able to leverage a single platform for identity governance, privileged access and to collect audit logs for compliance, making setup and management easier, while enhancing the user experience. Customers can enable end-to-end identity governance processes across applications, infrastructure and APIs at any level of scale using San Francisco-based Okta’s extensible APIs and no-code workflows.
Okta Identity Governance harnesses popular workplace tools to promote delegation and self-service, streamlining the evaluation and decision-making of who should have access to what resources and when. It automatically suspends access to resources based on user status changes in HR systems and directories and can produce quick audit evidence and reporting for sensitive resources.
Okta Privileged Access allows for the application of fine-grained user and role-based security policies from a central system to manage who can access what at the infrastructure level. It minimizes the attack surface area of privileged accounts and credentials by offering just-in-time, least privilege access controls, and streamlines compliance by tying session logging to specific users in a centralized view.
Optiv Managed Extended Detection and Response
Optiv Managed Extended Detection and Response debuted in August and ingests data across various layers of technologies to correlate, normalize, enrich and enable automated responses to malicious activity in real time. By automating incident investigations with actionable insight, organizations can detect threats faster and prioritize which threats to mitigate first, thereby reducing the attack surface.
The product is integrated into an organization’s current security technology to gather events, enrich the event data and escalate potential threats. From there, Optiv MXDR can identify the threats that matter to ensure rapid investigation as well as determine the severity, impact, affected assets and root cause of the attack, properly assessing business risk.
Optiv MXDR leverages Security Orchestration, Automation and Response (SOAR) to respond quickly, eliminate threats and administer containment actions with runbook development. Security incidents are managed to completion by Optiv MXDR with corresponding after-action reviews, according to the Denver-based company, No. 25 on the 2021 CRN Solution Provider 500.
Palo Alto Networks Okyo Garde
Palo Alto Networks Okyo Garde debuted in September to deliver security to remote workers‘ homes and small businesses, combining hardware, software and security services into a single subscription. It provides superior Wi-Fi speed and coverage, protection from malware, ransomware, and phishing attacks, and can be controlled through a simple mobile app, the Santa Clara, Calif.-based company said.
Okyo Garde gives small businesses the cybersecurity protection they need with ransomware and malware prevention, phishing protection, infected device detection, and suspicious activity monitoring and control. It can be ordered with the Okyo Concierge service, designed to provide peace of mind for small businesses by providing installation, 24/7 support or on-site troubleshooting, the company said.
For larger companies looking to protect remote employees, Okyo Garde will be integrating with Prisma Access to extend their corporate networks and bring unified security policy management and SASE to work-from-home employees. The work-from-home employee can also use Okyo Garde to enable an additional separate, private Wi-Fi network for the rest of their home and family‘s needs.

SentinelOne Singularity Mobile
SentinelOne Singularity Mobile debuted in December as a new AI-powered mobile security offering delivering autonomous threat protection, detection, and response for iOS, Android, and Chrome OS devices. Singularity Mobile’s industry leading on-device behavioral AI detects and protects against mobile malware, phishing, exploits, and man-in-the-middle (MiTM) attacks, according to the company.
Singularity Mobile customers can now manage mobile device security alongside their user workstations, cloud workloads, and IoT devices. The technology delivers mobile threat defense that is local, adaptive, and real-time to thwart mobile malware and phishing attacks at the device, with or without a cloud connection, according to Mountain View, Calif.-based SentinelOne.
Singularity Mobile provides deployment flexibility, including robust mobile device management (MDM) integrations and standalone configuration. With Singularity Mobile, powered by Zimperium, SentinelOne’s Singularity XDR platform has now expanded to deliver Mobile Threat Defense coverage to iOS, Android, and Chrome OS.
Sophos XDR
Sophos XDR debuted in May and synchronizes endpoint, server, firewall and email security to provide a holistic view of an organization’s environment with deep analysis for threat detection, investigation and response. The platform offers two types of data retention, including up to 90 days of on-device data as well as 30 days of cross-product data in the cloud-based data lake.
Blending on-device and data lake forensics provides contextualized insight that can be leveraged by security analysts through Sophos Central and via open APIs for ingestion into SIEM, SOAR, PSA and RMM systems. The data lake hosts critical information from Sophos’ endpoint, network, email, cloud and mobile products and is expected to feed into the company’s data repository, according to Sophos.
Security and IT teams can easily access this data to run cross-product threat hunts and investigations as well as to drill into granular details of past and present attacker activity. The availability of offline access to historical data further protects against lost or impacted devices, according to Oxford, U.K.-based Sophos.