The 10 Coolest New Cybersecurity Tools And Products Of 2020 (So Far)
The 10 cybersecurity tools and products making noise in the market have emphasized workflow automation, asset protection and downtime minimization to better safeguard clouds, endpoints and mobile devices.

Securing The Future
See the latest entry: The 10 Coolest Cybersecurity Tools and Products in 2022 (So Far)
Vendors have spent the first half of 2020 advancing security everywhere from the cloud to the endpoint to mobile devices, debuting tools that quarantine and remove malicious attachments, deliver protection across public and private clouds, and protecting users against unsuitable and malicious web content.
Enhancements to security operations and intelligence have been a major area of focus thus far in 2020, with advancements around automating workflows to speed detection and response, delivering actionable insights to improve asset protection, and minimizing downtime and restoring business operations.
Six of the 10 coolest cybersecurity tools and products of 2020 (so far) came from companies based in California, three came from companies based in other parts of the United States, and one came from a company based abroad. Read on to learn how suppliers have gone about making their cybersecurity portfolio even more solution provider friendly.

Cisco SecureX
Cisco SecureX was announced in February to provide more visibility across the entire security portfolio, delivering security analytics and automating workflows to speed threat detection and response. The platform unifies visibility across customers’ security portfolio in a cloud-native platform, delivering detection of unknown threats and policy violations via security analytics for more informed actions.
The platform automates common security workflows, including threat investigation and remediation, for more precise and efficient operations, according to Cisco. Cisco SecureX analyzes events and data across the enterprise, including from more than 150 million endpoints as well as network traffic from switches and routers, public clouds and private data center environments.
Within minutes, Cisco SecureX can identify who and what has been targeted and enable remediation using data enrichment across security products and threat intelligence feeds. The company said its new platform also brings the power of Cisco Talos threat analysts into the customer’s SOC to hunt for the latest threats.

CrowdStrike Endpoint Recovery Services
CrowdStrike Endpoint Recovery Services debuted in February and combines the power of the CrowdStrike Falcon platform, threat intelligence and real-time response to accelerate business recovery from cyber intrusions, the company said. The new service enables customers to rapidly mitigate security incidents and resume business operations with minimal interruptions, according to CrowdStrike.
CrowdStrike said Endpoint Recovery Services accelerates the standard life cycle of incident recovery, saving businesses from expensive downtime. Endpoint Recovery Services combines CrowdStrike Falcon, endpoint visibility from Threat Graph and experienced security analysts to ensure immediate attack disruption and comprehensive endpoint remediation, according to the company.
Endpoint Recovery Services stops attacks to minimize downtime and restores business operations without having to reimage or reissue endpoint devices, enabling customers to focus on recovering other critical business components. The initial phases of the service are focused on understanding the incident and deploying the Falcon platform without the need for on-premises visits or installations.

Cybereason Mobile & Cybereason Mobile MDR
Cybereason in April expanded its prevention, detection and response capabilities from traditional endpoints to mobile devices to allow customers to combat threats from a single console. Cybereason Mobile and Cybereason Mobile MDR provide more robust protection against mobile-centric threats like phishing than existing tools, which are typically more focused on setting policy than actual defense.
Cybereason Mobile deploys a sensor on mobile or point of sale devices to detect information and send it back to the company’s cross-correlation engine, allowing inferences to be drawn on the back end, according to the company. Cybereason said it’s looking to integrate and develop more sensors in point of sale and operational technology (OT) environment to drop more information back into its data lakes.
Meanwhile, the company said Cybereason Mobile MDR is a fully managed tool that provide around the clock monitoring and robust incident response capabilities for customers and partners lacking the skillset or manpower to support this through their own SOC (Security Operations Center). In fact, Cybereason said it can even help with deploying the sensors on employees’ mobile devices.
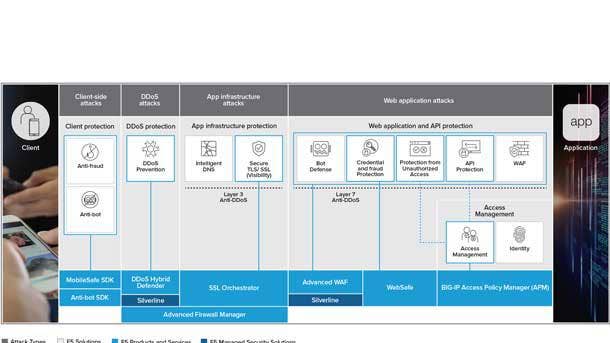
F5 Application Protection
F5’s Application Protection portfolio was unveiled in February to safeguard all applications without impacting the user experience or impeding the delivery of digital services from code to customer, the company said. The company said it has realized operational efficiencies by seamlessly enabling application security across multiple environments with consistent policies and controls.
F5 said its offerings guard against application threats such as application-layer denial of service, malicious scripting and injection attacks, with Shape Enterprise Defense mitigating attacks tied to app fraud and abuse. And the F5 identity-aware proxy enables single sign-on and multi-actor authentication policies to help organizations realize the benefits of modern authentication and authorization protocols.
The company also offers a managed service focused on DDoS through Silverline to help protect customers from volumetric or reflected amplification attacks. From there, F5’s intelligent threat services use advanced analytics to transform the data sets into tactical intelligence that is both relevant and consumable by portfolio services.

FireEye Mandiant Threat Intelligence Suite
The FireEye Mandiant Threat Intelligence Suite was introduced in February and offers incremental tiers of bundled offerings to help companies on their journey to intelligence-led security. The Intelligence Suite provides firms with a significant decision advantage to help reduce security risk whether security is someone’s part time job or the organizations already has a dedicated threat intelligence team in place.
Organizations are increasingly looking to reduce their risk and augment their security with external threat intelligence services, FireEye said. However, many organizations don’t know where to start, FireEye said, while others have jumped right in without understanding what threat intelligence they need or how it should be used, which too often makes the process both ineffective and costly.
The Mandiant Threat Intelligence Suite is available in standard, advanced and enterprise tiered bundles, according to FireEye. The company said its Mandiant Threat Intelligence subscriptions and services are intended to give organizations visibility and actionable insights to improve their protection of assets, enhance the effectiveness of security programs and inform business risk assessments.

Fortinet FortiGate 1800F
Fortinet in February upgraded its network processor for the first time since 2012 to provide the building block for hyperscale applications, delivering performance and fast connections across the board, the company said. In fact, the FortiGate 1800 firewall with NP7 (network processor 7) technology is 14 times faster than the industry average for products at a similar price point, according to the company.
Firewalls traditionally sat on the perimeter of the network and were focused on protecting a single port at low speeds, processing information line by line to ensure rules were being applied consistently, Fortinet said. But NP7 is able to speed up the Fortinet 1800F to the point where it’s able to sit at the core of the network and support VXLAN by running every single port at light weight, the company said.
Fortinet started with the 1800F since it’s a midrange system with a single CPU and a single console, but as the company goes forward, it will move beyond the midrange systems and start to implement it across all firewalls. As that process begins over the next four months, the company said customers will be able to put firewalls in places they’ve never been.

Palo Alto Networks CN-Series
The Palo Alto Networks CN-Series is a containerized version of the company’s firewall that was unveiled in June to help network security teams ensure they’re compliant in container environments, and enable security at DevOps speed by speeding up the integration and provisioning process, according to the company.
Kubernetes is red hot right now, and Palo Alto Networks wanted a containerized form factor as part of their firewall to ensure both security and compliance. The CN-Series firewalls leverage deep container context to protect inbound, outbound and east-west traffic between container trust zones along with other components of enterprise IT environments, according to Palo Alto Networks.
The CN-Series can be used to protect critical applications against known vulnerabilities as well as both known and unknown malware until patches can be applied to secure the underlying compute resource. Applications are protected with the CN-Series in on-premise data centers like Kubernetes and RedHat OpenShift as well as the Kubernetes service from each of the big public cloud providers, the firm said.

Sophos Intercept X For Mobile
Sophos in January began protecting Chrome OS users against unsuitable and malicious web content for the first time with its rebranded Intercept X for Mobile offering. The new mobile security capabilities will address the huge explosion of Chromebooks in the education space and the emerging opportunity in the health care and general corporate spaces as the devices move upmarket and become more feature-rich.
Intercept X for Mobile can now determine if apps installed by students or teachers on Chrome OS devices have malicious intent or operate unethically through tactics such as “fleeceware,” according to Sophos. Fleeceware excels at exploiting loopholes in the rules of Apple’s App Store or Google Play to evade detection but behave in an unethical or deceptive manner.
Intercept X for Mobile scours App Store libraries to identify malicious activity, the company said, looking for apps that have been side-loaded onto a mobile device or smartphones that have been jailbroken to install an application. As hackers adapt new techniques in the mobile space to evade detection, Sophos said it is employing machine learning to identify things the company has never seen before.
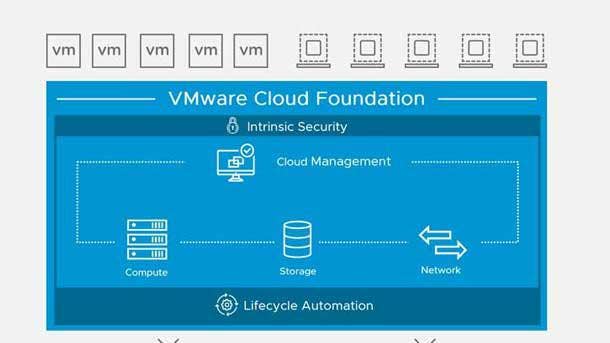
VMware Advanced Security For Cloud Foundation
VMware Advanced Security For Cloud Foundation was announced in February to address internal data center security challenges and deliver unified protection across private and public clouds, the company said. The offering includes VMware Carbon Black Workload Protection, VMware NSX Advanced Load Balancer with Web Application Firewall capabilities and VMware NSX Distributed IDS/IPS, VMware said.
The offering manages and gathers endpoint telemetry through built-in sensors protected by the hypervisor, meaning that attempts to gain root access and tamper with the product will be detected by the hypervisor. Meanwhile, the NSX Web Application Firewall uses a rich understanding of applications, automated learning, and application-specific rules to provide strong security with lower false positives.
In addition, VMware said the distributed architecture of NSX Distributed IDS/IPS enables advanced filtering to be applied to every part of the application, eliminating the blind spots associated with use of traditional perimeter security products. Policies are automatically generated and enforced on an application-specific basis, which VMware said lowers false positives.

Zix Secure Cloud
Zix combined the security and compliance offering from its 2019 acquisition of AppRiver with its own in April to create a single platform that safeguards digital communication tools. The company said it spent $20 million to develop Secure Cloud, which vastly improves upon a loose integration rolled out in July 2019 to make Zix’s intellectual property available to AppRiver partners.
A lot of work has been done at the application level to improve Secure Cloud’s advanced threat capabilities touching upon everything from sandboxing and messaging protection to integrations with SIEM (Security Information and Event Management) platforms. Up until now, Zix’s technology was mostly focused on protecting against phishing, malware and business email compromise (BEC) attacks.
Another new security feature with Secure Cloud is time of link click protection, meaning that a destination link in an email is scanned at the time the link is clicked to ensure there’s not malware on the site even if the email itself is from weeks or months earlier. Secure Cloud can also quarantine and remove a malicious attachment sent to multiple mailboxes in one fell swoop, according to the company.