Unisys CEO Peter Altabef On Security, Cloud, IoT

Security At The Heart Of Modernizing Customer IT Infrastructure
For a solution provider to grow to an annual revenue approaching $3 billion, nearly 85 percent of which comes from services, it must be doing something right. And at Unisys, that something is a maniacal focus on security as customers push hard to adopt the cloud, IoT, artificial intelligence and other technologies to prepare their digital infrastructures to meet future needs.
Peter Altabef, chairman, president and CEO of Unisys, told CRN that his company has made security the keystone of its services. He said Unisys' ClearPath Forward is the only operating system environment which has never seen a forceable extraction of data, as shown by the National Institute of Standards and Technology survey. And he invites people to try to break it.
Here’s a look at how Unisys is helping customers prepare for the future.

Unisys has transformed over the years from a mainframe focus to one of the world's top IT services companies. How would you describe Unisys today?
Unisys is a technology solutions company. We are a B2B company. And what distinguishes us in the verticals that we play in, the customer-identified client verticals, is an extraordinarily focused approach to make sure that all of our solutions include security. We have a suite of security solutions that are dedicated security solutions. But in addition to that dedicated suite, our non-dedicated security solutions all have security built in. It's our goal as a company to continue to enhance that. And in terms of the verticals that we play in, about half of our revenue is from governments around the world, about a quarter is from financial services providers, and the other quarter is travel and transportation, health care, life science, and a more general commercial set of customers. But I would say the thing that really distinguishes us is a real dedication to focusing on security.

Software is a big part of Unisys' business. What is your approach to that market?
[We use] software as a driver into our solutions. I'll give you an example. [Unisys] Stealth is part of our security suite of solutions. Stealth has a biometric identity component. It has a microsegmentation component. And we will sell Stealth as a license if somebody just wants to put it into their environment as Stealth, as a lot of companies do. But we will also include Stealth in a larger set of offerings. To give you an example, we signed a contract with the Transportation Safety Administration, or TSA, last year. And that involved strengthening the security and maintenance of their servers and laptops and hardware, really all around the world. It was a large contract. It was over $100 million. But Stealth was a very important piece of it because we were able to use that Stealth software to really lock down the network that these computers use. …
I usually say that we are a software-driven services company.
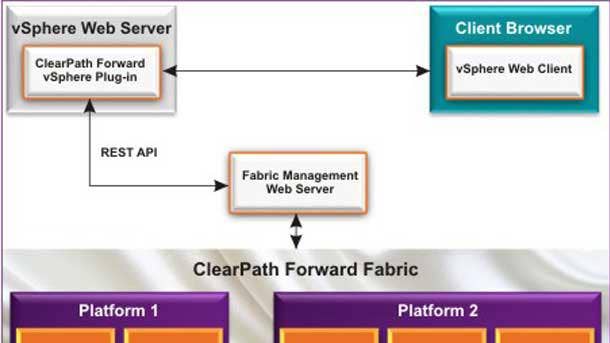
How about security in Unisys' ClearPath Forward operating system environment?
[ClearPath Forward], which is all x86 Intel, and which also operates in private and public clouds, is a very secure, very high-performance system. It runs some of the largest banks in the world. It runs some of the largest government agencies in the world, as well as some commercial clients.
You may be familiar with the NIST [National Institute of Standards and Technology] survey? Every month, NIST publishes a list of all of the major operating systems, and how often those operating systems have been the subject of data extrusions, people going in and taking data out. And as you can imagine, that's commonplace in the world that we live in today. Except for us. ClearPath Forward, in the history of the NIST survey, which goes back well over a decade, has never had a forceable extraction of data. So when we talk about Unisys really focusing on security even before it was cool to do so, that's a pretty good example.

How does one harden an operating system to the point where NIST says no breaches have occurred?
Even though 85 percent of our revenue is in IT services, in many ways, the core of the company, the DNA of the company, is in engineering. Our goal is not just faster, cheaper. We are really focused on designing better solutions. And those solutions have an internal integrity to them because we have this engineering focus that tends to be extraordinarily stable and difficult to mess with. That's why it's so difficult to hack. Our Stealth solution around microsegmentation—we hold hackathons around the world. Nobody in our hackathons have ever been able to get into Stealth. It's a very powerful part of what the company does.
But when you say nobody's been able to hack into it, isn't that an invite for somebody to try it?
Be my guest. In this world, you don't need to invite people to hack your systems. They do it on their own. But that is the approach we take to dealing with our clients. The confidentiality of data is just a critical part of running companies, of running government agencies. It is very much top of mind.

Public and private clouds are among clients' most pressing issues. How big a part of Unisys' business is from the cloud?
A very substantive part. Our solution for that is called CloudForte. We were the first provider to help a U.S. government agency get to the cloud. The very first one. Whether it is working for governments around the world, or working for companies, we think it's really critical that they utilize the public cloud as well as hybrid cloud environments. I think anybody that is fighting that effort is fighting a losing battle.
That said, all of computing will certainly not go to the public cloud. But it is, and should be, an integral part of almost any organization's strategy. What products like [Unisys] Stealth do is not only encrypt data at rest, but also encrypt data in motion. Stealth not only protects the data inside either the public cloud or private cloud, but also protects the data in the journey between the two clouds. ... Migrating to the cloud doesn't mean leaving the stuff in the cloud.

Artificial intelligence is also a fast-growing trend. Is Unisys seeing demands from customers to provide expertise or leadership in terms of AI?
I'll give you an example. We have a very substantive global workspace solution called InteliServe. This is our work on behalf of our clients to maintain the security of the data that exists in laptops and servers, as well as in Apple Watches and telephones and tablets. [InteliServe] includes a help desk feature for the people using those devices with respect to their data. We do this for millions of people around the world. We do it in over 100 countries around the world. And in that effort, artificial intelligence is absolutely critical because you constantly have to be learning, to constantly be understanding the data, so that if you see an issue, whether it's a security issue or a technical issue or even a hardware issue, if you see an issue arising in one area of the world or in one application or one company, you've got to analyze it very quickly. You want to understand from a predictive standpoint where is it going next and how do you get ahead of any issues.

So artificial intelligence is an important part of Unisys' security services?
Artificial intelligence is a boon for that. It's a boon for predictive analytics. And therefore it becomes very important for us. That's one example. But it really is table stakes. I would say, in the last 24 months, blockchain has become table stakes, too. And blockchain can be an important element in securing a supply chain. And supply chains are critical. Very few companies make everything that they sell. And very few companies are not extremely dependent on supply chains. So the more you can secure the providence of your supply chains, the better. And blockchain is perfectly suited for that.

Given that about half your customer base is government, how does Unisys apply blockchain technology?
Governments are really interested in supply chains. Think about government use of technology products. And think about where they're concerned about making sure that the products they use are not counterfeit. Think about the concern of the components in the products they use, and the integrity of that. That's pretty important to governments right now.
And think of other clients. Think of a government agency in the agriculture business, and how important it is as they're helping citizens understand the provenance of food as it goes from farm to market to grocery store to home. Those are typical examples of how governments around the world are very, very focused on understanding supply chains. Blockchain is simply a tool that you can use when doing that.

How about IoT? Is that coming up yet in conversations with your clients?
Almost table stakes. I wouldn't say it's quite table stakes yet, but almost table stakes. When we first approach a problem, the first thing we think about is, what's the business solution that you're trying to achieve, and then how do we achieve that solution in a secure way. The big challenge for IoT devices is many of the devices out there are not firmware-upgradeable. And those that are firmware-upgradeable don't tend to get upgrades. And so, from a hacking standpoint, you really have an issue with how to secure IoT devices. There's a lot of work going on in the community itself about that. [We can put our Stealth technology] inside those IoT devices and protect those IoT devices and the network that those devices are using. … But you have to be able to do that in a very light-touch way, because by definition these devices don't have a lot of memory, and have very limited ability to be upgraded.
So IoT is important to Unisys' solutions?
IoT is clearly important. I think the current estimates are that within five years there'll be 20 billion devices. So it's going to be really important. And as those devices are really kind of consumer devices, I think someone will develop an Underwriters Laboratories-type of approach to IoT devices, and there'll be some minimum standards of security and upgradeability. And there'll be a ‘UL’ for IoT devices that will give people surety that they will have the basic ability to be upgraded.

California is already working on regulations to prevent devices from being shipped with a standard password, or pushing users to change passwords when the devices are installed.
California has been on the forefront of several of these efforts, including how to deal with GDPR-type issues that are already top of mind in Europe. And you're seeing it expanding to other places around the world.
For a company like Unisys, which deals with clients and governments across the U.S., do state-specific regulations such as those proposed in California make it more difficult to do business?
It's actually an advantage for Unisys. We work with 300 governments around the world. State governments in the U.S., as well as state, local and federal governments around the world. … The complexity of working with governments is, honestly, something we specialize in. It's not that we celebrate when standards are different. But we certainly know how to handle differing standards. And because we work in so many of the states in the United States, we're particularly attuned to how you see these standards develop over time. …
States are [often] laboratories for developing new administrative solutions. So it's not a bad thing. You tend to see over time, as these standards begin to coalesce, the federal government wanting to take it over. And that's fine. But the fact that states are at the forefront of being creative in some of these areas, and are a little more nimble at some times, is actually a good thing for the country.

We recently saw HCL acquire a large part of IBM's software portfolio. How does that impact the IT services industry in which Unisys plays a part?
HCL's an interesting company. I have decades of familiarity with them. It's an intelligent company. And I think that what they're doing with that acquisition is emblematic of what I [have referred to as] a software-led services organization. When I use that term, that's really what I think HCL is trying to do. And it's exactly what we have been doing for the last several years. In a large, consolidating market, one of the ways you distinguish yourself is not just doing your best for less, but really bringing solutions that have a fundamental architecture to them that can be leveraged, because you've invested in the solution, and then you can roll it out with modifications to multiple companies. I think that's behind what HCL is doing, and that's behind what we've been doing for several years.