The 10 Coolest Cloud Security Tools Of 2021 (So Far)
The 10 coolest cloud security tools to hit the market in 2021 (so far) can discover critical data located in the public cloud, centrally manage Amazon Web Services EC2 instances in real-time, and visualize and prioritize cloud security risks.

Locking Down The Cloud
Read the latest entry: The 10 Hottest Cloud Security Tools and Products of 2022
Vendors have made great advances thus far in 2021 around securing cloud applications, data, and workloads, rolling out tools that can discover critical data located in the public cloud, centrally manage Amazon Web Services EC2 instances in real-time, and visualize and prioritize cloud security risks to reduce the attacker’s blast radius and facilitate faster investigations.
Securing customer and workforce identity has been a major area of investment, with companies provisioning just-in-time access to hybrid and cloud servers and making it possible for all users and devices to securely access cloud, mobile, SaaS and on-premises applications and APIs. Other vendors, meanwhile, have focused on automatically discovering and preventing risks for new SaaS applications.
Four of the coolest new cloud security tools come from companies based in California, four come from companies based in the Northeastern United States, and companies based in Colorado, Michigan and France each contributed one offering to the list. Read on to learn what new cloud security features and functionality partners are now able to enjoy.
For more of the biggest startups, products and news stories of 2021 so far, click here .

Blumira AWS Security Monitoring
Blumira launched Amazon Web Services security monitoring into its cloud security platform in May, giving customers greater visibility and control over the security of their entire technology stack. The company’s monitoring of AWS GuardDuty, CloudTrail and VPC Flow Logs helps users find and remediate risks like publicly exposed S3 buckets that can result in data leakage and compliance violations.
The Ann Arbor, Mich.-based company’s technology monitors attack patterns, analyzes billions of events for malicious activity, and surfaces contextual data needed to reduce the noise, time and manual effort spent on investigation. This enables small IT and security teams to quickly respond to indicators of an attack in progress such as account changes, potential malware infection, and abnormal cloud infrastructure behavior, Blumira said.
In addition to AWS, Blumira’s cloud security monitoring and reporting tool integrates across both on-premises and cloud services like Microsoft Office 365, Azure and Google Workplace (formerly G Suite). Blumira said it protects against cloud threats such as attacker login attempts, data leakage, device malware, and other malicious behavior that could result in a ransomware infection or data breach.

Cisco Meraki SD-WAN Fabric
The Cisco Meraki team in March extended its SD-WAN fabric into the cloud edge to simplify Internet Protocol Security (IPSec) tunnel connectivity and avoid maintenance and orchestration challenges. IPsec isn’t the best mechanism for reliably connecting a physical location into the cloud due to concerns around IP address changes or failovers.
The SD-WAN and cloud security integration leverages analytics and performance monitoring to fully automate and orchestrate decision-making when it comes to traffic routing, ensuring traffic goes through the right tunnel and cloud entry point based on performance and latency metrics.
As a result, San Jose, Calif.-based Cisco can take its SD-WAN technology with multiple tunnels, redundancy and reliability and extend it all the way into the cloud. Cisco demoed the integration between Meraki and Umbrella during a keynote in March, and intends to create a similar fabric extension for Viptela in the future.
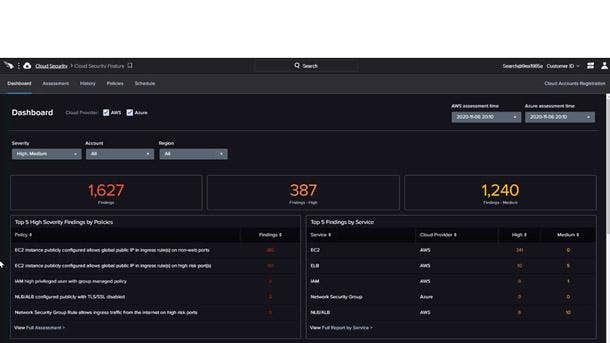
CrowdStrike Falcon Horizon
New Falcon Horizon features unveiled in May leverage CrowdStrike’s telemetry to deliver indicators of attack for the cloud control plane and provide DevOps tools for faster detection and remediation. The new capabilities include continuous threat detection, and monitoring and correlation across cloud and on-premises environments to help security teams cut through the noise of a multi-cloud environment.
Falcon Horizon’s new CrowdStrike Confidence Scoring continuously aggregates, assesses, and scores cloud control plane threats and changes in configuration to accurately identity malicious activity. The scores help security teams prioritize the most urgent threats, allowing them to identify, understand and act against critical threat activity and avoid sifting through inconsequential alerts.
Falcon Horizon enables faster integration and remediation with organizations’ DevOps and collaboration tools, seamlessly onboarding new cloud accounts through Sunnyvale, Calif.-based CrowdStrike’s API. The offering also provides simplified management and security policy enforcement from a single console, eliminating blind spots, preventing security incidents, and ensuring application availability for any cloud.
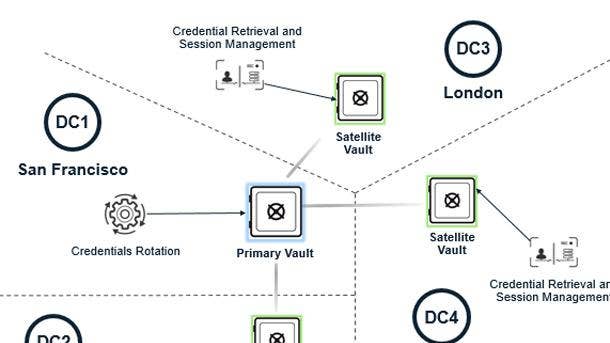
CyberArk Dynamic Privileged Access
CyberArk Dynamic Privileged Access implements time-bound just-in-time access and significantly reduces standing access for Windows and Linux servers. The service works seamlessly alongside CyberArk Privileged Access Manager to provide the most comprehensive platform for securing both standing and dynamic access for human and machine identities from hybrid to multi-cloud.
The service was announced in June, and is designed to provide privileged access granted just-in-time, significantly reducing the risk caused by standing access to organizational environments. Newton, Mass.-based CyberArk’s Dynamic Privileged Access defines who can access what based on company joiner, mover, and leaver changes, as well as the dynamic lifetime and business context of an organization’s assets.
CyberArk Dynamic Privileged Access enforces strong, adaptive, multi-factor-authentication for identity and establishes isolated and recorded sessions to an organization’s environment. Members of an organization can connect natively using existing authentication methods while enforcing a large variety of multi-factor-authentication methods using personal credentials in a native, browser-less fashion.
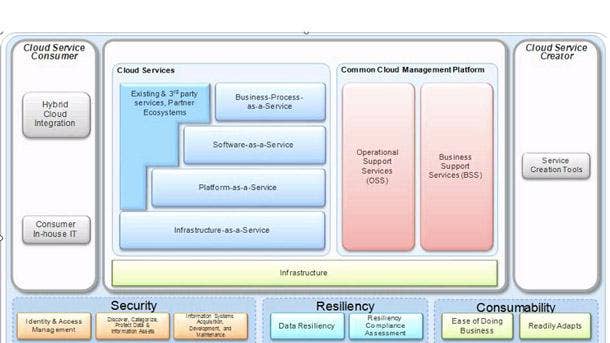
IBM Security Hybrid Cloud Blueprint
The IBM Security Hybrid Cloud Blueprint helps organizations modernize their security program with visibility and control over the most sensitive data and activities as they migrate to the cloud. The blueprint makes it possible for organizations to enable continuous compliance, reporting and response, monitor for cloud misconfigurations, and build consistent policy enforcement across all cloud workloads.
As part of this blueprint, customers can choose to purchase IBM Security Services for Cloud, which offers an open, automated approach to help simplify hybrid cloud security. The Cambridge Mass.-based business unit introduced this offering in May, which brings together cloud-agnostic security expertise together with an integrated set of cloud, proprietary and third-party technology solutions.
Meanwhile, IBM Cloud Pak for Security now combines leading capabilities in threat management and data security into a single, modular, easier to consume offering. And the new IBM Cloud Pak for Security as a Service provides access to a unified dashboard across threat management tools, with the option to easily scale with a usage-based pricing approach.
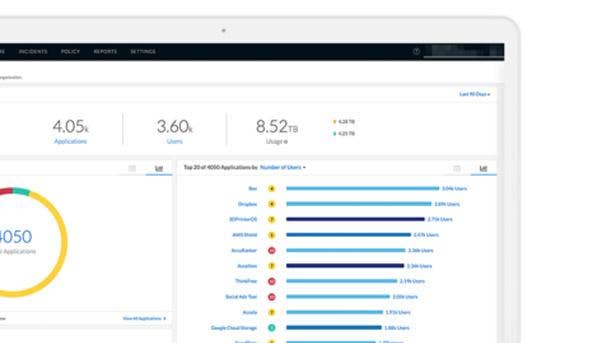
Palo Alto Networks SaaS Security
Palo Alto Network SaaS Security is a cloud access security broker (CASB) introduced in May which proactively protects both on-premise and cloud-hosted applications. It automatically discovers and prevents risks with thousands of new Software as a Service applications before they become a problem, according to the company.
Continuous identification, categorization, and granular risk-based control of known and previously unknown SaaS applications is provided through App-ID technology, ensuring new applications are discovered automatically as they become popular. Palo Alto Networks SaaS security integrates natively into the company’s hardware as well as its next-generation firewalls.
Meanwhile, Santa Clara, Calif.-based Palo Alto Networks’ Cloud Identity Engine is designed to consistently authenticate and authorize users regardless of location and where user identity stores live. This empowers organizations to move toward a Zero Trust strategy and provides them with access to applications and data in the cloud, on-premises, or in a hybrid model.
PingOne Cloud Platform
The new PingOne Cloud Platform was unveiled in June and gives companies a single point from which to manage every Ping Identity product and service in their security arsenal. The company updated and unified its entire portfolio in the cloud to solve enterprise challenges around workforce and customer identity.
The platform enables unified digital identities and allows all users and devices to securely access cloud, mobile, SaaS and on-premises applications and APIs. For enterprises that require maximum uptime, Denver-based PingOne’s Advanced Services are hybrid and can be deployed in multiple clouds for failover and redundancy.
PingOne for Customers enables companies to simplify the lives of users with single sign-on, multi-factor authentication, and other identity services that significantly improve security. PingOne for Workforce, meanwhile, enables companies to adopt cloud identity quickly and easily through a central authentication authority in the cloud that delivers one-click, single sign-on access to any user.
Thales Data Protection For Multicloud Environments
Thales’ new data protection offerings for Google Cloud, Microsoft Azure and Amazon Web Services debuted in May and allows firms to bring their own security to the cloud and solve challenges around discovering critical data, reducing operational complexity, and ensuring data sovereignty. The offering allows clients to maintain control of their encryption keys and manage cloud access and authentication.
Thales Data Discovery and Classification now automates the discovery, classification, and protection of data in AWS S3 buckets and Azure Blob storage through encryption of tokenization. The Paris, France-based company now encrypts Kubernetes secrets and Google Anthos Service Mesh signing keys, and leverages CipherTrust Transparent Encryption access controls to protect data in AWS S3 buckets.
Thales is also offering CipherTrust Cloud Key Manager support for Google Cloud’s External Key Manager, making it easier for customers to manage more encryption keys across multicloud environments. Plus SafeNet Trusted Access now integrates out of the box with Google Workspace, Azure and AWS to enforce appropriate access controls and authentication for privileged and regular users.

ThycoticCentrify Cloud Provider Solution
ThycoticCentrify’s cloud provider solution came out in May to centrally manage Amazon Web Services billing accounts, identity and access management (IAM) accounts, and AWS EC2 instances in real-time. It extends a set of existing privileged access management capabilities to automate continuous discovery of all AWS EC2 instances, providing full visibility of instances even in elastic auto-scaling groups.
AWS root/billing accounts are vaulted for emergency access only, and interactive access to AWS Accounts via the AWS Management Console, AWS CLI, SDKs, and APIs is controlled, said ThycoticCentrify, headquartered in Washington D.C. and Santa Clara, Calif. AWS IAM accounts and associated Access Keys are eliminated or vaulted to reduce the attack surface, with SAML-based federated single sign-on providing a more secure and lower maintenance alternative.
Continuous EC2 discovery and post-discovery automations allow for complete and accurate visibility, ensuring that EC2 instances and their privileged accounts are immediately secured and brought under centralized management. ThycoticCentrify’s cloud provider solution is initially available for AWS and will soon be extended to Microsoft Azure and other cloud provider platforms.
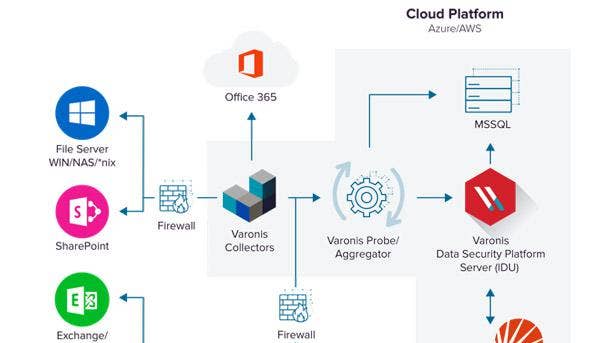
Varonis DatAdvantage Cloud
Varonis DatAdvantage Cloud was unveiled in May to visualize and prioritize security risk, allowing clients to see and prioritize their biggest cloud risks, proactively reduce their blast radius, and conduct faster cross-cloud investigations. It correlates identifies with privileges and activities across cloud stores, including Amazon Web Services, Box, GitHub, Google Drive, Jira, Okta, Salesforce, Slack and Zoom.
DatAdvantage Cloud provides a clear view of permissions across an organization’s cloud services with recommendations to eliminate excessive, inappropriate, or unused privileges. It prevents cloud account takeovers, insider threats, and inadvertent policy violations with cross-cloud auditing and alerts on suspicious activity and policy violations.
Cloud events can be normalized and enriched with DatAdvantage Cloud to allow security analysts to investigate incidents cross-cloud without having to craft complex, service-specific queries, said New York-based Varonis. DatAdvantage Cloud can also automatically link accounts across disparate cloud services to form a single identity while easily uncovering over-privileged shadow accounts both human and non-human.
Advertisement