Wipro Attackers Breach PCM And Hit ServiceNow, Others: Reports
The attacks against 11 major worldwide solution providers and IT vendors seem to have been aimed at gathering resources including customer names and IT platforms that would provide ways to steal money via gift cards and convert it to currency.
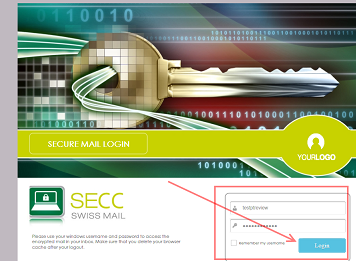
The Lucy log-in screen that was modified for use in the attacks.
The cybercrime group that went after India-based Wipro and a group of other solution providers managed to breach solution provider PCM, according to a report by Krebs on Security.
The group also attacked a slew of technology companies including ServiceNow, ZoomInfo and GFI Software earlier this year, according to an analysis by cybersecurity firm RiskIQ.
Krebs on Security Thursday reported that PCM, an El Segundo, Calif.-based solution provider, in mid-May discovered it had been breached, allowing hackers to access several of its clients' email and file sharing systems.
[Related: Tata Consultancy, NTT Data Among Cloud Hopper Attack Victims: Reports]
As a result of that attack, attackers stole administrative credentials used to manage client accounts. The attackers seemed to be interested in information that could help conduct retail and financial gift card fraud, a PCM client told Krebs on Security.
PCM told Krebs on Security that the impact of the breach was limited and the issue was mitigated. PCM did not respond to a CRN request for information by press time.
Insight Enterprises earlier this week said it is acquiring PCM.
In a related development, several big-name IT vendors and large global solution providers were attacked in the latest in a string of what appears to be attempts to breach their security and grab customer information for potential financial gain, according to a report by San Francisco-based digital threat management technology provider RiskIQ.
The attacks were originally reported in April as targeting Wipro, and later that month the subjects of those attacks grew to include other solution providers including Avanade, Capgemini, Cognizant, Infosys, PCM, Rackspace, and Slalom.
However, according to RiskIQ, a fifth round of attacks took place between January and May of this year, and in addition to those eight companies were also directed at ServiceNow, ZoomInfo, and GFI Software.
RiskIQ also said the breach attempts were launched at over 40 other companies worldwide in the financial transaction processing, reserve, and clearinghouse; retail, restaurant, and travel; employee rewards and corporate loyalty; and digital marketing and Communications industries.
RiskIQ said it is unknown whether any of the breach attempts were successful.
The breach attempts seemed to be aimed at gaining financial benefits for the attackers, RiskIQ said.
In analyzing the attacks, the company said the attacks against traditional retail organizations could provide access to gift cards as a way to gain assets outside of traditional western financial systems. The attacks against company and employee reward programs could give the attackers broad access to gift card-based rewards. The attacks against gift card providers and processors could give attackers access to a way to convert gift cards into currency and help transfer funds. Attacking digital marketing companies could provide attackers with platforms and services for distributing phishing emails. And attacking IT firms could provide access to multiple companies via third-party providers, RiskIQ said.
The attacks were carried out by using phishing pages to attack targets with generic login forms, all of which were similar except for the target companies' logos, and were generated by a phishing software package identified by RiskIQ as Lucy.
The RiskIQ report was the second report of major security attacks against solution providers and their customers. Earlier this week, Reuters reported that NTT Data, NTT Data subsidiary Dimension Data, Tata Consulting, Fujitsu, and DXC Technologies were all victims of attacks whose data, systems and customers were compromised by the years-long CloudHopper attacks from 2014 to 2017. The CloudHopper attacks were initiated by Chinese state-sponsored hackers, Reuters said.
None of the IT vendors or solution providers contacted by CRN replied to a request for further information by press time.