SentinelOne CEO On Microsoft’s Security Copilot: ‘It’s A Nice Chatbot’
In an interview with CRN, SentinelOne Co-Founder and CEO Tomer Weingarten says his company’s use of generative AI for security stands apart from what Microsoft and Google are doing in the space.

Weingarten On The Record
Around the cybersecurity industry, numerous vendors have debuted new products powered by generative AI in recent months, in a bid to capitalize on the red-hot technology initially popularized by OpenAI’s ChatGPT. So far, however, some of the uses of generative AI for cybersecurity have been more substantive than others. And when it comes to SentinelOne’s generative AI-powered threat hunting tool, Purple AI, the “astounding” product is clearly leading the pack, according to CEO and Co-Founder Tomer Weingarten.
The tool is the first in a series of planned products from SentinelOne that will be powered by generative AI, and “I think for us, it’s a whole new way to reimagine cybersecurity,” Weingarten said in an interview with CRN at the RSA Conference 2023. For security analysts, the technology ultimately enables them to “traverse through more data with more speed, with more accuracy — and just automate away a lot of the grunt work in cybersecurity.”
[Related: Generative AI Is Going Viral In Cybersecurity. Data Is The Key To Making It Useful.]
By comparison, Microsoft’s initial foray into utilizing generative AI for cyber defense, with its Security Copilot tool, is “incredibly limited,” Weingarten said. And while Google Cloud’s offering in the space is closer to what SentinelOne is doing, it’s still not on par in certain key respects, he said.
All in all, Weingarten said it’s no coincidence that SentinelOne has been able to unveil a truly powerful tool applying generative AI to cyber defense — and do so more quickly than others. “We were talking about AI, and we were integrating neural networks into our product, for years,” he told CRN. “When you have the ability to train models, when you have the big data infrastructure, when you have all the expertise of the data scientist teams that have been doing this for years — then yes, it’s easier for us to do it.”
During the interview, Weingarten also discussed the massive opportunity he sees for SentinelOne in cloud security and the company’s exclusive partnership with Wiz, a fast-growing startup in the segment.
What follows is an edited portion of CRN’s interview with Weingarten during RSAC 2023, which took place in San Francisco in late April.

What’s the No. 1 issue you’re focused on at the conference this week?
The amount of vendors, the amount of solutions, the solution sprawl, environments entrenched with so many different products, all working in silos — that’s the biggest issue in cybersecurity. Security is complex enough as it is, and if you spread it across 100 different products, then it becomes even more complex. So it’s almost like we’re shooting ourselves in the foot by trying to put more and more products out there. [Customers need] a more seamless experience.
I would sum it up in one word — it’s value. I think that’s what we’re trying to create in a much more tangible way. [With] the economic downturn, it’s all about extracting more value in what you have.

How does your partnership with Wiz help to accomplish that for SentinelOne?
You get compounded value by joining two separate parts of cloud security into one cohesive fabric that will be easier to manage, and will enrich each one of these different elements of cloud security.
[Wiz] has built a phenomenal cloud inventory visibility platform, that for a lot of the public cloud users, just gives them unfettered visibility into their entire footprint. And to us, it was always a missing piece — where we can secure that footprint for you, but we don’t always see and scan and find that footprint. That was kind of their concept. So if you take their ability to see everything you have in the cloud, identify what could benefit SentinelOne protection — and now have one-click deployment to all of it, and get back the alerts into one place, get enrichment to all of it — then you have a whole new way to think about cloud security in a very seamless way.
Now, we don’t do all of that today. So we just announced the first phase of integration. But hopefully by the end of the year, we can create that completely automated experience for cloud security. So you can imagine customers getting better security hygiene, better visibility, more bang for their buck — because now they can also protect what they see, and they can see what they need to protect. That’s what we hear from customers — they are super, super interested. Everybody’s asking us, ‘Can we start deploying this? Can we do this? Can we do that?” And we’re trying to kind of rein them back in, because we can’t do everything just yet. But I think it’s showing great promise. [For] about a third of our business, we focus on cloud. Obviously we do more than cloud security. But in that third of the business, that’s just a great pillar for us to double down on.

You recently said you see the cloud security opportunity as potentially being even larger in the future than endpoint security. Could you say more on what makes you think that?
Everybody’s in some stage of their journey [to the cloud]. No one is fully migrated to public cloud. So you get into these environments where part of what they do is on-premise, part of what they do is in the public cloud. And I think this partnership [with Wiz] actually helps bridge that gap. Because our workload protection isn’t designed to be only for the cutting-edge public cloud environment or containerized environments — you can actually deploy it on-prem as well. [And in] Linux environments, classic virtual machines. So it’s an amazing bridge for companies out there that are thinking, “Part of my stuff is on-prem, part of my stuff is in the cloud. How do I wrap my head around all of it?” I think that by joining forces, you get best-of-breed public cloud visibility, get the on-prem [coverage] with us. So it’s just a great way to accompany these customers in their journey to the public cloud.

What are the next phases for the SentinelOne-Wiz integration?
We just announced the ability to get Wiz context data as a threat is detected, via the SentinelOne platform. So that’s a great first part. Because obviously, when someone gets a threat detection or an anomaly detection in the cloud, they want to understand what environment it happened [in] and what is it tied to? And this is just a beautiful capability that they’ve built, which is they can map out the entire thing for you. They can stitch together all these different attack paths, or how things are tied [together] in the cloud. So you mesh together the AI-based detection that we do with their full context of the cloud.
The next stages are to do the opposite as well — so, enrich Wiz’s data with any type of threat data from SentinelOne. Deployment [will be another focus] — so just having the ability to do one-click deployment. Our sellers already are getting up to speed with selling their platform. I think those are our goals for this year. I think we can shoot even higher. I would love to integrate all their telemetry and have Purple be able to parse through it. So you could ask Purple about your cloud security posture, as an example. And I think that will be another way of making data incredibly accessible for the customer. We might be able to nail that this year, maybe we won’t. But we have stretch goals.

What’s the opportunity for channel partners with this?
We have one of the most robust channel ecosystems. If you couple what the MSP ecosystem can do with a product like Wiz’s, and what the overall channel distribution that we have can now do with a joint offering — then you also start to understand that it’s a force multiplier for [partners] as well. They now come out with a best-of-breed offer. It’s the best workload protection you can find, plus the best security posture management you can find. So now you just have a winning offering if you’re a channel partner selling into a customer environment. I think it’s very hard to compete against what we have jointly together.

Could you talk a bit more about Purple AI and why you see that as such a major advancement?
Purple is the future. I think for us, it’s a whole new way to reimagine cybersecurity. What it can do — even today in the limited preview that we put out there — is astounding. It takes any entry-level analyst and makes them a “super analyst.” We train the algorithms with so much security operations data that you virtually create a machine-human analyst with unlimited scale — because you’re not limited by the amount of flesh and blood that’s behind it.
And it’s a know-all being with whatever you feed it. And it works at speed that a human can’t. And in security, all these things just mean that you can traverse through more data with more speed, with more accuracy — and just automate away a lot of the grunt work in cybersecurity.
I think one of the most interesting parts in Purple — beyond the fact that you can just ask it any question in plain English, or in any language almost — is that you [don’t only need to] ask it questions. As an analyst, sometimes you ask about what you can contemplate. And what Purple does, beyond just answering the question for you, is it proposes other questions that you might not have thought of. By looking at your environment and knowing what’s there, it can actually suggest follow-up questions. So if you’re an analyst and you were asking about a specific operation — maybe APT39 — but there’s no activity of that in your environment, it might [suggest], “Maybe ask about APT41, because I might be seeing some indicators there.”

Are there other differentiators with Purple that you’d want to highlight?
The follow-up actions are also remarkable — because basically, it will tell you what to do next. Once you ask the question, you got the results — for instance, you’ve got 50 affected endpoints — it will suggest what the correct action is to potentially take now. So not only you can now, with one click, start remediating your environment — and do it with no scripting, no coding. You can also choose to take that action now automatically in the future, again, every time that these conditions are met. So you’re turning a question into a real-time rule that can now be evaluated as new data comes in and is being parsed. So it revolutionizes the SIEM, it revolutionizes the SOC, it revolutionizes SOAR. It’s going to be a simpler world for all of us.
I think that with Purple, it’s currently the most advanced algorithm out there [for security]. Obviously we’ve seen Microsoft with [Security] Copilot, which is a nice chatbot. I don’t entirely get what they’ve tried creating there, besides saying that they have it. But what it can do is incredibly limited and doesn’t touch the actual security data that you have. And you’ve seen Google put security analytics out there, which is a relatively similar concept to what we launched as well. But for us, having that ability to tap into endpoint, cloud, and all these different separate disciplines is something that Google can’t do currently.
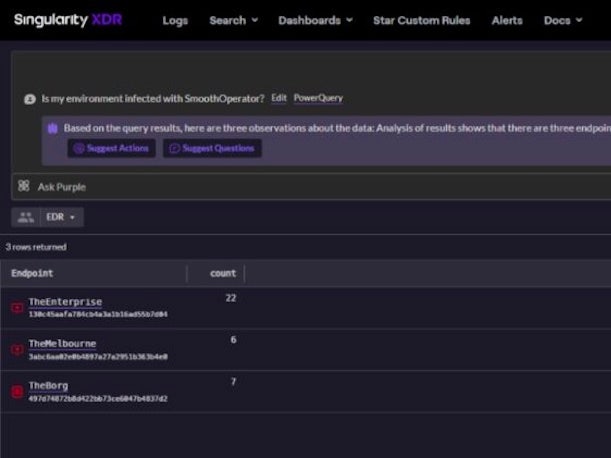
What are you looking at in terms of where to go next with Purple?
We’re working with two things right now. One is the user experience, and the other is the scale. [In terms of] the LLM algorithms, GPT-4 is definitely one of the best ones out there. We’re experimenting with multiple [LLMs]. We’ve used GPT-4, we’re also using Flan-T5 by Google. We’re exploring Anthropic, we’re exploring Cohere. A lot of these [LLMs] have really, really good models. But I think it really is more about training the algorithms, and less about the algorithms themselves. There was a pretty robust research report by Stanford on all these different algorithms, I think ranked around 40-something different parameters, and you can see how they perform. It’s not a secret. And I think that a lot of them are robust. Some of them are not as robust. I think we would opt to eventually use an algorithm that’s open-sourced. We truly believe that to build something ethically structured, you’ve got to have visibility into how it’s working. I think explainability and the rationale behind what’s happening behind the scenes, that’s what will create transparency and trust in these models. Because otherwise it’s going to be really, really hard to just assume that it does the right thing for you. All these models are going to have to have a degree of explainability to them.
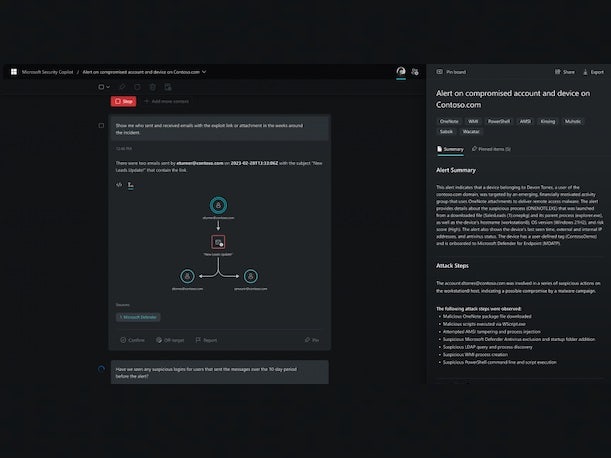
In terms of Purple AI actually being embedded in your products, do you see that as a key difference from what Microsoft is doing?
Part of the power of this is just having a unified approach, where it’s directly embedded in what you do. It sits on top of the data lake so that it has access to all the data that you put in. We announced at RSA that you can now put into the data lake, every other product telemetry that you have in the enterprise — basically from the Palo Alto [Networks] firewall that you have, or Check Point or Fortinet, or into your email provider, or your identity provider. Now Purple can answer questions from all of these different sources. And that’s where it becomes just immensely powerful.
And it’s going to get better as we train it more. It’s going to get better with more human interaction — because part of it is also the reinforcement learning. So obviously, the more you give it feedback or whether it was accurate enough, or you wanted to see something else, it learns in real-time to be better at what it does. So again, when I say scale, with scale also comes the accuracy and just additional value. It’s what gets these systems better — they’re not stagnant.

Since your focus has been on AI-powered, autonomous security for a long time, would you say that’s what allowed you to release a tool like this faster than others?
Totally. We were talking about AI, and we were integrating neural networks into our product, for years. And I think that for many people, AI might have been just a buzzword you put out there. But for us, it’s what was driving detection — and what is driving detection today — across 10,000 customers. In some of the most demanding environments, we’ve got an autonomous algorithm embedded into the endpoint agent that can detect and prevent threats in real-time in a completely heuristic, machine learning-driven way. So when you couple that capability with a large language model — when you have the ability to train models, when you have the big data infrastructure, when you have all the expertise of the data scientist teams that have been doing this for years — then yes, it’s easier for us to do it.