AWS CISO On Why Its Security Strategy Tops Microsoft, Google
‘We’re not playing checkers, we’re playing chess. And we’re playing chess at 150 miles per hour, on the internet, with everybody watching,’ says CJ Moses, a cloud cybersecurity pioneer and CISO at AWS.

Cybersecurity Guru CJ Moses: ‘We’re Not Playing Checkers, We’re Playing Chess’
From chasing terrorism cybersecurity threats across the globe at the FBI to playing a lead role in creating the world’s first virtual private cloud, CJ Moses says Amazon Web Services owns the most secure cloud on the planet.
“We’re not playing checkers, we’re playing chess. And we’re playing chess at 150 miles per hour, on the internet with everybody watching,” said Moses, AWS’ chief information security officer and vice president of security engineering, in an interview with CRN.
AWS’ CISO said his Seattle-based company is at the top of the cybersecurity cloud pyramid versus Microsoft Azure and Google Cloud due to AWS’ security culture, adopting strategies learned from Moses’ “paranoid life” working for the FBI and the Air Force Office of Special Investigations (AFOSI).
Moses was hired by Amazon CEO — and former AWS CEO — Andy Jassy 15 years ago with the purpose of bringing his cybersecurity expertise and engineering skillset from working at the FBI and U.S. Air Force Office of Specialist Investigations (OSI) to AWS.
“[Amazon Chief Security Officer] Steve Schmidt and I came on board with our history of chasing hackers around the wild west of the internet, doing all the things we did around nation-state threat actors, counterterrorism work, and we were given the opportunity to build the technical infrastructure to be able provide the most secure cloud in the world,” said Moses.
“The reason why I can say that is we built it from scratch. We built the culture. We took the security culture that we had from our paranoid life at the FBI and OSI and all these things, and integrated it with the ownership model that is part of the core Amazon environment and culture,” he said.
[Related: AWS Marketplace’s ‘Incredible’ New Vendor Insights Tool: 5 Keys]
AWS Run Rate Hits $79 Billion
Last week, AWS reported a 33 percent spike in sales year over year for in its second quarter 2022, with total revenue hitting $19.74 billion.
The worldwide cloud market leader now has an annualized run rate of a whopping $79 billion. This historic benchmark comes as Amazon pours billions into new data centers to extend its national and international cloud reach as demand for AWS cloud services soar.
Keeping customer networks, data and entire IT environments safe is paramount for Moses and the security team at AWS, he said, as seen with various new security launches at AWS re:Inforce last week.
In an interview with CRN, Moses explains why AWS bests cloud rivals Microsoft and Google Cloud in the cybersecurity world, why cloud security is the future versus on-premise , and AWS’ overall vision.

Why do you think AWS has the securest cloud in the world compared to Microsoft and Google Cloud? Google Cloud, for example, just announced it would buy Mandiant for $5.4 billion.
Kevin Mandiant [founder and CEO of Mandiant] was my partner at OSI [U.S. Air Force Office of Specialist Investigations].
Kevin and I worked together at the FBI on an investigation when he was there at Air Force OSI, so Kevin and I are good friends and have been forever.
First off, we don’t bolt security on. We built it from scratch.
Every service team that’s been hired, has been hired with a security culture in mind. So that’s every individual person that’s part of the team.
[For example] when we do acquisitions, that’s the one area where we have to go in and actually rewash acquisitions sometimes to make sure that they have the security culture. You get the Amazonian culture, it’s part of that, but then the security culture of, ‘How do you think about doing things?’
If you’re a software development engineer in AWS, it’s part of your day-to-day responsibilities to be thinking about the things that you’re doing and making sure that they’re secure.
That’s the differentiator—having the culture from day one, carrying it forward, building the infrastructure and all the services and everything was built thereafter—was built with security not only in mind, but as job-zero.
Straight up, the number one thing you got to do is security.
Andy Jassy and Adam Selipsky have made that very clear over the years in weekly security meetings.

Talk about AWS’ security-first IT culture and how you created it.
Steve Schmidt (pictured), myself and a handful of others were at the FBI with a need for a capability. That capability had to be highly secure and dynamically scalable.
The mission was that we had to take every piece of digital media the U.S. government got for counterterrorism purposes, cross-correlate it against everything else we knew in history. And basically, find the needle in the haystack that was going to keep bad things from happening to good people.
You can imagine back in those days, it was big data before there was big data. Our mission was to figure out how to—when the digital truck showed up at Friday at 4:30pm—how to go ahead and find that piece of data that was going to keep bad things from happening to good people.
We didn’t have the technology we needed in order to make it happen quicker. No matter what we did, it couldn’t scale enough.
We launched EC2 as the very first iteration. We’re like, ‘That’s exactly what we need: Elastic Compute Cloud. 1,000 computers for an hour is much better than the inverse of that.’
From that time, the discussions flipped, because they weren’t ready to provide it for us. Andy Jassy said, ‘The only way we’re ever going to get there as we bring people like you on board in order to build that capability from scratch.’
Steve Schmidt and I came on board with our history of chasing hackers around the wild west of the internet, doing all the things we did around with nation-state actors, counterterrorism work, and we were given the opportunity to build the technical infrastructure to be able provide the most secure cloud in the world.
The reason why I can say that is we built it from scratch. We built the culture. We took the security culture that we had from our paranoid life of FBI and OSI and all these things, and integrated with the ownership model that is part of the core Amazon environment and culture.
Single threaded leaders own success and failure, profit and loss—security is part of that. That’s not just a saying. The reality is you’re in a meeting, that single threaded owner owns the security of each and every service. They’re not saying, ‘It’s CJ’s job. Why isn’t CJ here getting yelled at?’ It’s their job to make sure their services are secure. That’s part of the culture that we helped create and carry forward over the years.
The same thing applies to everything that’s been built from day one.
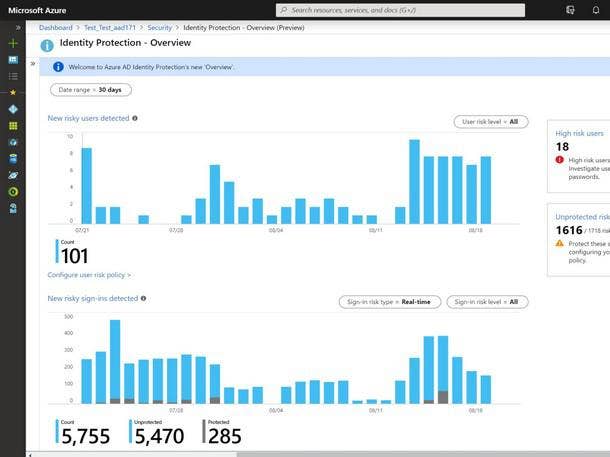
Microsoft has seen some systemic security issues in Active Directory, password breaches, and difficulty in securing on-prem and cloud. Why isn’t this happening to Amazon?
It’s because of the foundation we built and how we are making investments forward.
Perfect example is the issues that we saw in various different intrusion issues or otherwise supply chain issues over the last year or so: we don’t present Active Directory to the internet, because we understand that there can be issues there.
We’d rather not have a single layer of defense that we don’t own there.
We do use Active Directory, just like anyone who runs Microsoft at any scale does. We actually have our own, what we call midway—our own capability that we use that’s an enabler to our zero-trust capability, and multi factor authentication, and all that. That is our gateway to the internet or gateway to outside of our own environment.
That’s why we made that investment years ago. We had to spend the money, take the time, do the research, build the capability, but because we did all of that in advance, it paid off later on.
That’s exactly what you’re seeing in a lot of these different cases is: we’re not looking for the threat of tomorrow. We’re looking for the threat cases and vulnerability cases that are out years ahead.
You’ve heard Andy Jassy say this, but there is no compression algorithm for experience.

Amazon CEO Andy Jassy
Can you dive into Andy Jassy’s saying, ‘There is no compression algorithm for experience’?
We bring the experience of having seen these things happen elsewhere. And we know how bad actors are going to try to get into the environments.
There’s always a human behind the keyboard. These things aren’t happening randomly off computers doing things. These things are humans with intent behind them.
Figuring out what the intent of the human is, and then being able to thwart that by looking ahead as to how would we find our way in or how could these things happen? There’s people with skills that know how to do those things so you should use those skills and thwart them on the front end.
We don’t wait for the threats to be there. We look forward.
It’s a cat and mouse type of game that goes on forever—but we’re playing the long game. We’re looking further out.
We’re not playing checkers, we’re playing chess. And we’re playing chess at 150 miles per hour, on the internet, with everybody watching.
But that’s the speed we’re used to operating at. So it’s not uncomfortable for us. That’s the environment that that we like to operate in.
That’s why we keep highly charged people with way too much caffeine in there.
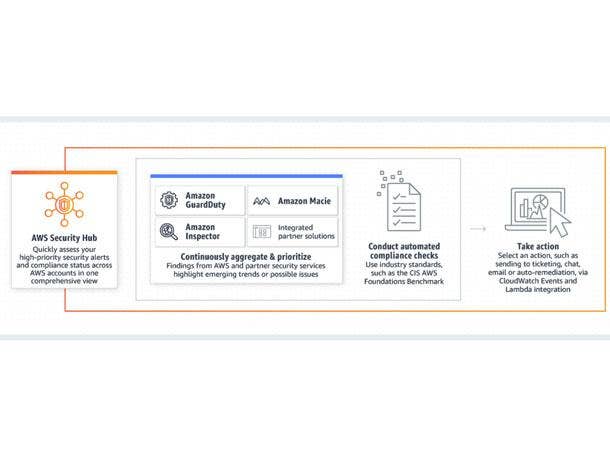
Can you talk about cloud security versus on-premise security?
You never want to be at a disadvantage to an adversary, and being on-premises and having adversaries that are using the power and capabilities that are provided by the cloud and cloud capabilities, you find yourself to be at a disadvantage.
So using the cloud to secure the cloud is exactly what we’ve done.
When we started building AWS 15 or 16 years ago, and then when Steve and I came on board, we built the infrastructure, and the culture, even more so to be able to enable our environment to be the most secure cloud in the world.
Because we saw what the internet was. We saw the wild, wild west that it was when we chased hackers around the globe, quite literally.
In that process, we realized that if we ever had the opportunity to build a bigger, stronger, better internet that could be truly secured, we would take that opportunity. AWS presented that opportunity.
Now that you’ve seen that transition and we’ve seen more cloud adoption, and continuing to go down that road—we’re still day one.
Because, I mean, what percentage of IT is in the cloud these days? I think our numbers are around 5 percent. So they’re still 95 percent of IT workloads are still not in the cloud. So there’s still that much more to go.
Now having the focus of security providers from our ecosystem, the things that we’re doing with that focus—we’re going to continue to see enhancements. Because now you have those security organizations and teams that used to be focused on-prem now focusing on the cloud because of the things that can do with creating new capabilities.
When you start to bring all of that together, you start to see the scaling effect that’s beneficial.
You used to be really worried and provide security at the network layer. As long as you had that nice network protection, everything inside was protected—you can’t do that anymore.
If you’re not protecting your data at the data level, you’re leaving layers of opportunity for adversaries to make their way in. And we’re not going to do that. We’re paranoid about security.
What’s one security philosophy that helps AWS stand out from your cloud rivals?
We actually have security trained ambassadors for the service teams called ‘Security Guardians’ so those teams don’t have to come to our security, they’re going to have their own security engineers in many cases.
We take those engineers and make sure that they are as closely aligned with us as they can be. So that if there’s questions, normally they’ll ask their Guardians within their own environment.
It also means is that when it comes time that they’re creating a new service, or have something that’s going to get retrospective review from a security perspective, we’ll go ahead and work with the Guardian, the ambassador if you will, to make sure everything is good.
What we found is by doing so, there’s a greatly increased percentage of them going through the review without any real findings. So it’s a big reduction, because they’re actually even that much more focused. We created that. You’re starting to see that now in a lot of places.
The previous model used to be that you’d have security people from a security team that we hire, and then we embed. The problem is that they’re always seen as outsiders.
So rather than do that, how about take people that are insiders, train them on security stuff that they should be looking for, and continue to maintain that relationship and that flow of information. Then grow and foster to make sure that they’re part of the embedded teams.

Why will AWS best Azure and GCP in security in the long run?
We believe in least privilege like crazy, to the point where I want to make sure that, as best we can, we create technology that not even my people nor I can access the data that’s on a server.
Rather than having administrators that secure shell into a box in order to do some sort of work, obviously these things have to be maintained, we have created chipsets or hardware that’s designed along the lines of being able to take out the management and control planes and separating them.
So your disk controllers and all that kind of stuff is separate from each other.
Now what the people that are running the infrastructure are doing, is they’re using API’s that have a very small attack surface and do not have the means by which to pull customer data out of the system.
It used to be, when you’re talking to a customer, ‘What contractual obligations do you have to protect me from insider threat of somebody getting access to my data?’
I’d rather put a technical control mechanism in place that prohibits us from being able to do so. Run your environment in a Nitro architectures—and we’re on multiple generations of that now we’ve been doing it for years—and you’re limiting our ability to actually ever be able to have access to that.
We’ve invested literally billions of dollars into doing things that previously were contractually based, into creating mechanisms and technical controls to prevent it from happening to begin with.
That’s why we’re more secure than others.
Because others don’t have that level of investment, that commitment, crazy paranoid people like Steve and I, or Andy Jassy and Adam Selipski, who are pushing us to continue down that road.
We’re going to continue to do that to the point where we’ll be in a situation where customers will be able to see everything that’s going on, and be able to audit it, and know all of the actions that are done on their behalf in order to run within the cloud.